Symmetric and Asymmetric Encryption: What to Choose and How It Works

Key Takeaways
- Symmetric encryption uses a single key for both encryption and decryption, making it efficient for large data.
- Asymmetric encryption employs a pair of keys: one public for encryption and one private for decryption, enhancing security.
- Hybrid encryption combines both methods to leverage speed and security, making it ideal for secure communications.
- Choosing the right encryption method depends on the specific needs for speed versus security in data transmission.
- Emerging technologies like quantum computing pose new risks to existing encryption methods, necessitating updates and adaptations.
Encryption is the magical transformation of data into a secret code, which can only be deciphered by those who have the correct “key.” In the age of technology, encryption has become the primary armor for protecting personal and corporate information from hacking. You encounter it daily: whether you are making online payments or communicating via messaging apps — your data remains secure. And by understanding the different methods of encryption, you can not only protect your data but also choose the most convenient way for your tasks.
What is Encryption?
Imagine your data wrapped in an invisible code, and only those with a magical little key can decipher it. That’s what encryption is. Today, it serves as your digital armor: whether it’s chatting with loved ones, shopping online, or storing important company data.
Encryption helps you stay calm, knowing that no intruder can access your files. It protects information on the Internet, in cloud storage, and on billions of devices. In the face of growing cyber threats, it’s like having an umbrella during a downpour.
The History of Encryption: From Ancient Times to the Present
Even ancient people knew how to encrypt! In Egypt, they devised clever symbols to send secret messages. The Greeks used a “scytale” — a wooden cylinder with texts wrapped around it.
During the Renaissance, Leon Battista Alberti invented the polyalphabetic cipher, complicating the decryption of messages. In World War II, Germany used the legendary “Enigma.” Despite its complexity, it was cracked by Allied cryptographers, marking an important milestone of the war.
Now everything has shifted to digital. Modern algorithms, such as AES and RSA, keep data completely secure, and encrypted messages are an integral part of messaging apps, banking operations, and even smart gadgets.
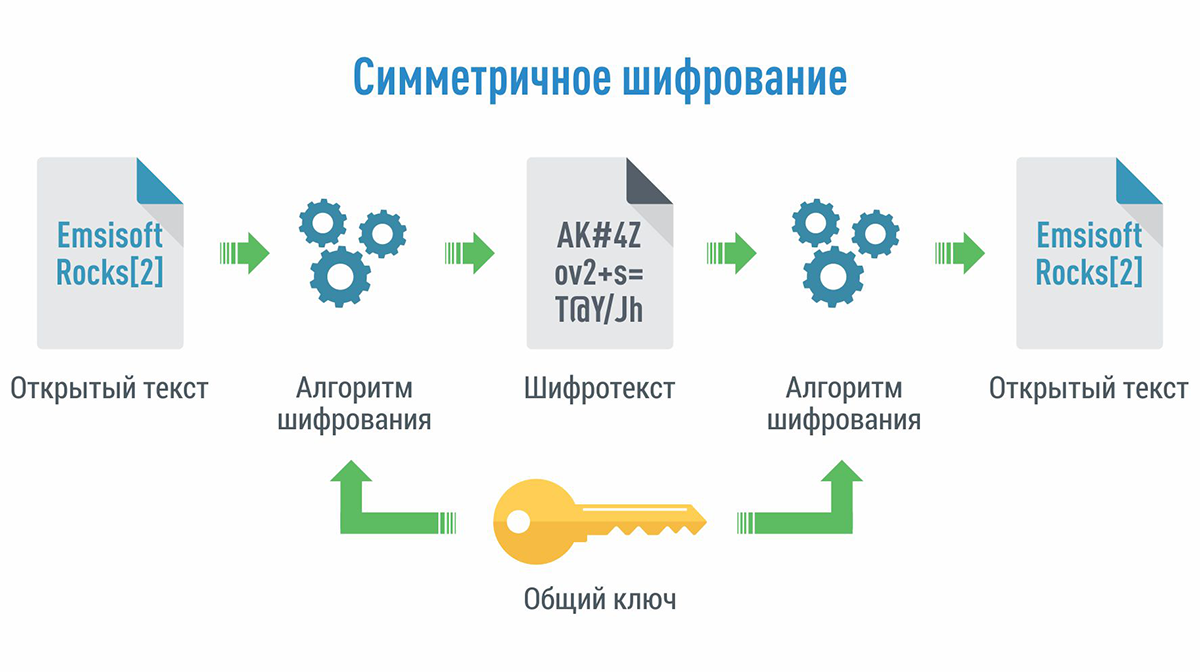
Symmetric Encryption
Imagine: you have a secret key that can both lock and unlock your “digital lock.” That is symmetric encryption. It’s simple, but sharing that key with someone else is a challenge, as its leakage jeopardizes everything.
Popular Algorithms
| Algorithm | Key Length (bits) | Block (bits) | Security |
| DES | 56 | 64 | Low |
| 3DES | 112 or 168 | 64 | Medium |
| AES | 128, 192, 256 | 128 | High |
| Blowfish | 32–448 | 64 | High |
How It Works?
- A key is generated, agreed upon by the sender and receiver.
- The sender encrypts the data, turning it into cipher text.
- The receiver decrypts the data using the same key.
Advantages: speed, simplicity, and resource efficiency. But there are downsides: the need for secure key transfer and the difficulty of scaling.

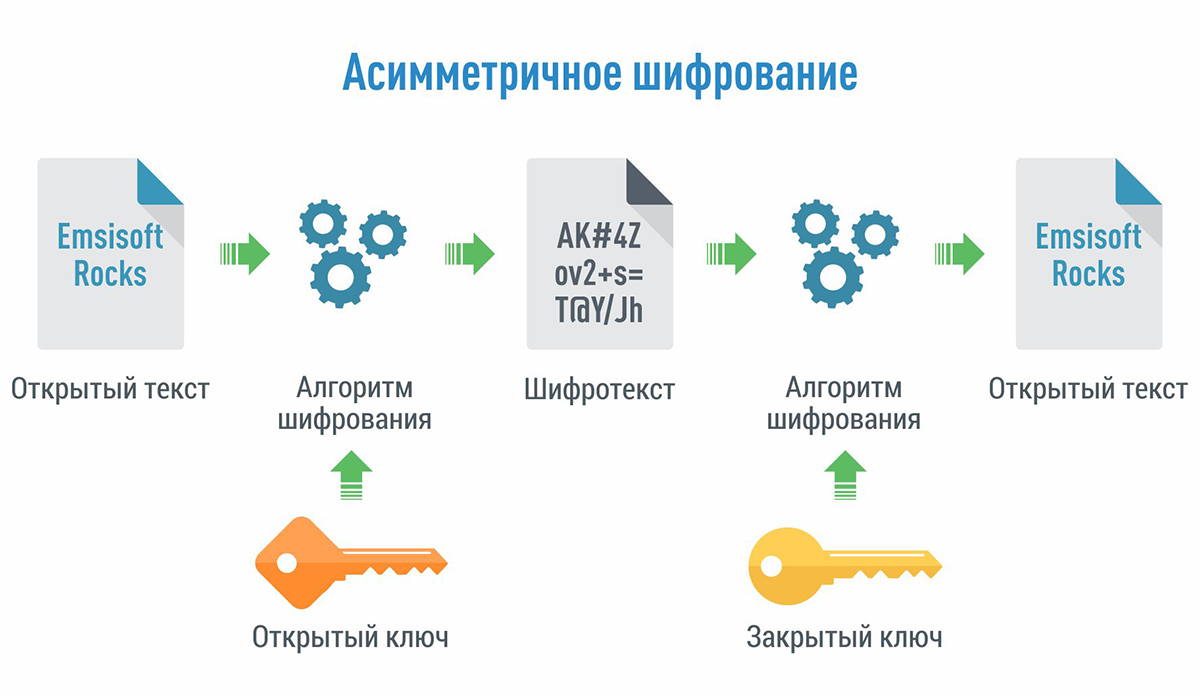
Asymmetric Encryption
This type of encryption works on the basis of a key pair: one public and one strictly secret. The public can be shared with anyone, but the private key must remain with you. This makes data transmission maximally secure.
Popular Algorithms
| Algorithm | Key Length (bits) | Security | Speed |
| RSA | 2048 and above | High | Slow |
| ECC | 256 | Very High | Fast |
How Asymmetric Encryption Works?
- Sending Data: the sender uses the recipient’s public key to encrypt the message.
- Transfer: the encrypted text is sent over the network.
- Receiving Data: the recipient uses their private key to decrypt the message and retrieve the original data.
Example: you want to send a secret message to a friend. They have a public key, which you use to encrypt the text. No one else can read it except your friend — only their private key will “unlock” your message.
Pros
- Super Secure — the private key is never transmitted, and no one can intercept it.
- Ideal for public networks, where the public key can be accessible to everyone.
- Used not only for encryption but also for authentication and digital signatures.
Cons
- Not fast — algorithms require more computational power and time.
- Large keys — especially with RSA. But ECC helps resolve this issue.
Examples of Use
- SSL/TLS: secure connections between users and web servers.
- Digital Signatures: confirm the authenticity and integrity of documents.
- Email Encryption: systems like PGP protect your correspondence from prying eyes.
Asymmetric encryption is like a Swiss Army knife in the world of cryptography. It is used for a variety of tasks where security and convenience are paramount.
What is the Difference Between Symmetric and Asymmetric Encryption?
The main distinction is the approach to keys. Symmetric encryption has one key shared by both parties, while asymmetric encryption uses a pair: one public and one private.
| Parameter | Symmetric | Asymmetric |
| Key Types | One Shared | Key Pair |
| Speed | Fast | Slow |
| Security | Medium | High |
| Where Used | Local Data | Networks and the Internet |
How to Choose?
- If speed is important — choose symmetric. It is suitable for archives, databases, and local files.
- If security is crucial — opt for asymmetric, particularly for data transmission over the Internet.
- And if you need both, a hybrid approach will combine their advantages.
Hybrid Encryption Systems
When both speed and reliability are needed, hybrid systems are used. They combine symmetric and asymmetric encryption, minimizing their weaknesses.
How It Works?
- In the first stage, asymmetric encryption is used to securely transmit the symmetric key.
- After the key is transmitted, data is encrypted using the symmetric method. This allows for quick processing of large volumes of information.
Example: SSL/TLS
- The client (you) encrypts the symmetric key using the server’s public key.
- The server decrypts the key using its private key.
- After that, data between you and the server is transmitted using symmetric encryption.
Why Is This Cool?
- Speed: data is encrypted quickly.
- Security: keys are transferred securely.
- Flexibility: suitable for large-scale projects and working in public networks.
Hybrid systems form the foundation of security on the Internet. Want safe online shopping or comfortable VPN usage? It’s all thanks to hybrid systems.

Risks and Challenges of Encryption
Even the most powerful encryption algorithms are not eternal. They can be broken not only by hackers but also by new technologies.
Main Threats
- Quantum Computing: future quantum computers will easily break old algorithms like RSA.
- Key Compromise: if someone obtains your private key, your data will no longer be secure.
- User Errors: weak passwords, improper key storage, or software vulnerabilities can render encryption useless.
How to Protect Yourself?
- Use long and complex keys — the more complicated the key, the harder it is to break.
- Update your algorithms — old standards like DES are outdated; choose modern ones like AES.
- Watch for quantum-resistant algorithms — this is the next step in data protection.
- Store keys securely: preferably in specialized modules or reliable software.
Encryption is not just protection; it’s a constant race against threats. The better prepared you are, the longer your data will remain secure.
How to Choose an Encryption Method for Your Project?
When selecting encryption, consider three factors: the volume of data, the level of security, and available resources.
- Big Data? Use symmetric encryption, such as AES, to quickly process large amounts of information.
- Need Reliability? Choose asymmetric algorithms like RSA or ECC for working on the Internet.
- Care about Both? Implement hybrid systems.
Examples
- For online payments, use SSL/TLS with a hybrid approach.
- For storing local data, AES is ideal.
- For secure chats, hybrid systems are suitable, like in messaging apps such as Signal.
Conclusion
Encryption is your armor in a world of digital threats. Symmetric methods are fast and effective, asymmetric ones provide the highest level of security, and hybrid systems combine the best of both worlds.
Your choice depends on what matters more: speed, reliability, or versatility. Make your selection wisely, and your data will remain under reliable protection, even as cyber threats grow more complex.
Earn with ECOS
Begin mining easily and safely with ASIC rental at the cutting-edge ECOS data center – an optimal solution for stable income!
What are the main differences between symmetric and asymmetric encryption?
Symmetric encryption uses a single shared key for both encoding and decoding information, while asymmetric encryption utilizes a pair of keys: a public key for encryption and a private key for decryption. This fundamental difference affects their respective speed and security levels, with symmetric being faster and asymmetric providing higher security.
Which encryption method is faster for data transmission?
Symmetric encryption is generally faster than asymmetric encryption due to its simpler key management and operations. Since it uses the same key for both encryption and decryption, it processes data more quickly. This makes symmetric encryption well-suited for applications requiring high speed and efficiency.
How can I choose the right encryption for my needs?
To select the right encryption method, consider the volume of data and the level of security required. For large data sets where speed is essential, symmetric encryption is preferable. In contrast, if secure key exchange and high-level protection are critical, asymmetric encryption should be used.
What are the risks associated with using encryption?
While encryption is a powerful tool for data protection, it is not infallible. Key compromise, where an unauthorized person gains access to private keys, can render encrypted data vulnerable. Additionally, being unaware of emerging threats, such as quantum computing, can put encryption strategies at risk.
Can I use both encryption methods in my projects?
Yes, using both symmetric and asymmetric encryption can be highly advantageous. This hybrid approach employs asymmetric encryption to securely share symmetric keys, combining the speed of symmetric encryption with the security benefits of asymmetric methods. It is commonly used in secure communications, such as TLS/SSL protocols.